(Estimated Reading Time: 8 minutes)
Why Build a Safe Malware Lab
The main reason to build a Malware Lab is to protect your primary computer(s) from infection by the malware you are analyzing. Using virtual machine software like VMWare, HyperV or VirtualBox is a very sensible solution to creating an isolated malware lab provided that your host computer is powerful enough to run a couple virtual machines. You could use physical machines but virtual machines have the distinct advantage of being easy to reset to a clean state after infection. Virtual Machines can save you a ton of time reloading Operating Systems (OS) and tools between analysis sessions.
So how many VM’s do you need? I’ve linked a couple good resources I found below. Two VM’s seems to be about the right number to get started with basic analysis. You need one VM to detonate the malware on (most likely a Windows VM), and another VM to fake out internet services like DNS, etc and record network traffic with WireShark. A REMnux Linux VM is the ideal setup for the second VM. You can grab this Linux distro, founded by Lenny Zeltser, here at the REMnux website. REMnux can be easily setup to run InetSims and can basically act as a fake C2 server for the malware.
When it comes to setting up the virtual machine to execute the malware in (ie detonate it) you will want to create an environment where the malware is mostly like to run as intended by the malware author. To achieve this you may need to install PDF Readers, or Office Applications if the malware was targeting those apps for example. You’ll also need to disable many of the Operating Systems security features, like antivirus software and so on. You’ll also want to install some tools into this virtual machine to capture changes made to the machine while the malware is running, like a Flight Recorder.
Approaches
So how do you go about setting up a virtual machine to execute malware in. There seems to be two approaches, and maybe a third hybrid approach.
- Build the virtual machine entirely yourself, install all the software manually, configure all the security settings, etc. The good thing about this approach is you pick exactly what tools you want to install, and you learn how to configure all the OS settings you need to change. The downside is this will take you the most time.
- Use a fully automated script. The most popular example I’m aware of is the FLARE VM from Fireeye. This is sort of like packing the entire kitchen sink for a weeks vacation. It includes all the tools you’d probably every want and then a few more. The downside is it take 30-40 minutes to install them all and it took about 100GB on my virtual machine when I tested this. I think this approach is great for someone with powerful hardware and someone experienced in using lots of the included tools. If you’re just getting started it may be a bit much.
- …and the third way is maybe a mix of both. SentinalLabs has a lightweight automated script, SentinelLabs RevCore Tool, that will install a handful of common tools and change the most common OS settings. Other tools you’d still install yourself. This is sort of a nice approach as the script runs fairly fast and contains the basic tools you need to get started.
I ended up going with two virtual machines for my first Malware Lab setup since I’m still learning. I used a Windows 10 virtual machine and manually installed the most basic tools, like sysinternals and a few others. For the second VM I went with REMnux and configured InetSims to provide fake network services. Overall I was happy with this setup and was able to easily walk through a couple malware tutorial samples from here and here using my setup, as shown in the image below.
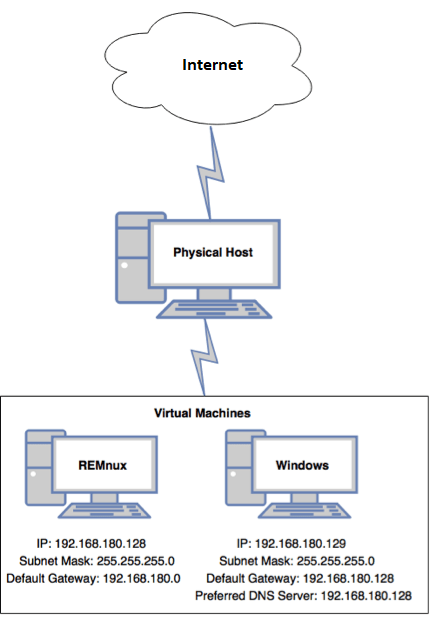
Is it safe to use to the same network and internet connection that I use for all my other devices and family things? A bit of an open question. I could introduce a firewall and VLAN but is that overkill for basic analysis? Curious what you would do? Comment on my twitter feed at @C00011011