(Estimated Reading Time: 11 minutes)
Why Look at Strings
Although it is not common for malware samples to contain clear text strings, it does happen, and it is an easy place to start analysis. Strings can be embedded in malware samples and provide indications to what the malware will do when executed. Strings can be looked at statically using tools without requiring the malware to be run.
I decided to take a benign sample from an online malware course, Lab01-01.dll, and run it through different string tools to compare the tools. The string tools I used are referenced below.
Example of Looking at Strings
To start out my analysis I surveyed several tools for dumping string information which I have summarized in the table below. I then ran each tool against my sample, Lab01-01.dll, and reviewed the output which I have summarized in the second table below.
| Tool | Type | Pro/Cons |
|---|---|---|
| strings.py | Python | Lots of great command line options, needs python but that is easy to install. Updated frequently with new features. |
| Strings2.exe | Executable | I could not get this tool to run with a long input filename path. When I copied the sample into the same folder as strings2.exe it worked. Standalone tool which is nice but not updated since 2017 it looks like. |
| BinText.exe | Executable | GUI tool that is easy to use, but strangely listed strings twice for some reason, more details on this below. Also looks like it has not been updated in a long time. |
| strings.exe | Executable | Well supported sysinternals tool. Easy to use. |
| IdaPro | Executable | GUI tool or IDAPython. Really over kill just for looking at strings but will do the job. |
| PEStudio | Executable | GUI tool with nice tips that help indicate why certain strings might indicate malicious behavior. Looks to be well supported and updated. Has a Pro version as well. |
| Hybrid-Analysis | Website | Easy to use web site but requires sample to be uploaded to the site. Will give you way more then just strings and may be overkill if only looking for a dump of strings |
| FLOSS | Python | Looks like it would be good based on this blog. It will try to statically decode strings and extract stack strings. I was able to run the 1.7 version by downloading the repository and running the standalone floss.exe binary. |
Using the above tools with their default options against Lab01-01.dll found the following number of strings.
| Tool | Strings Found | Notes |
|---|---|---|
| strings.py | 37 | Was fast and easy to use |
| strings2.exe | 37 | Was a bit tricker to run, but got the same result as strings.py |
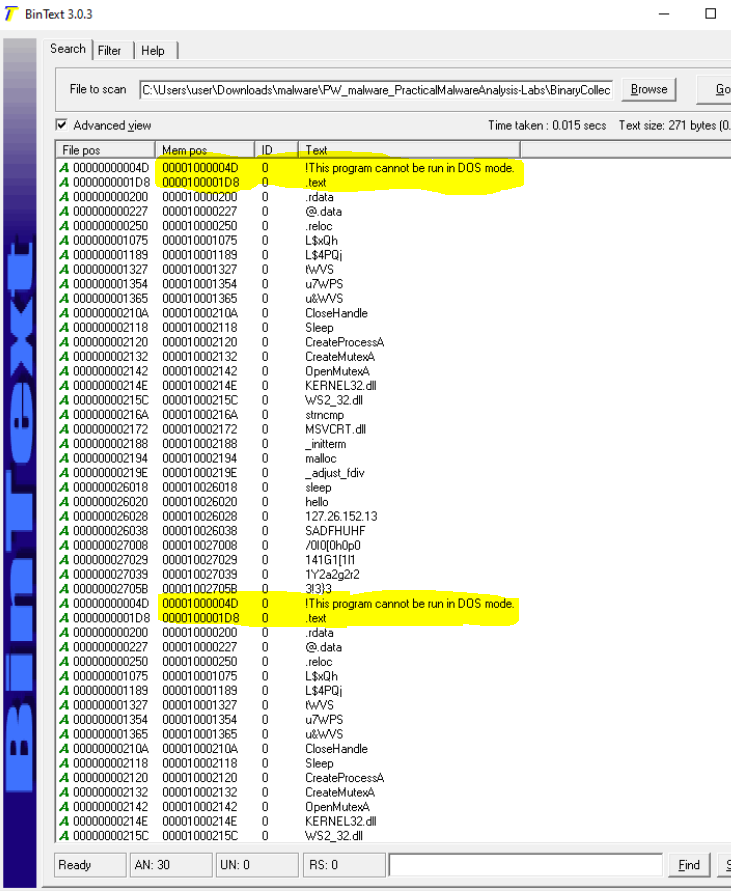
| BinText.exe | 60 | This was a strange case. I realized it was listing strings twice (doubling) so it really found 30 strings. See screen shot below showing the doubling. |
| strings.exe | 54 | Had a few additional strings over the prior tools but most the extra strings looked like garbage strings. |
| IdaPro | 8 | The free version of Ida listed 8 strings. |
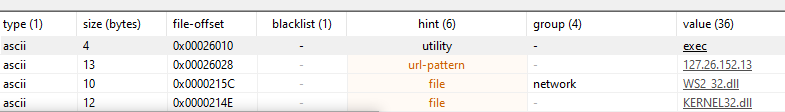
| PEStudio | 36 | Easy to use GUI with nice hints column that tries to tell you a little context about the string, like URL or file. See image below |
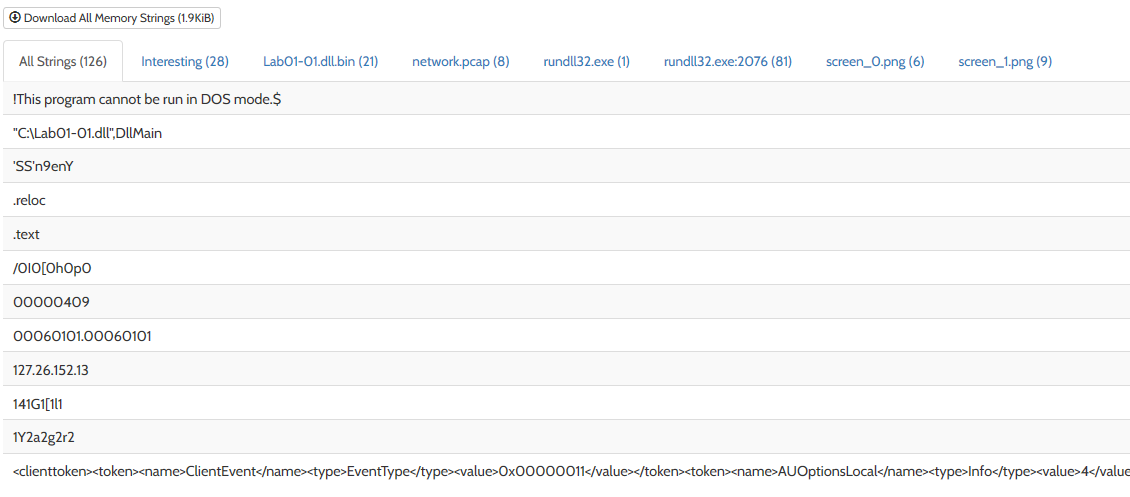
| HybridAnalysis | 126 | This site found 126 strings in this sample. I think it used both static and dynamic analysis so it found additional strings at run time. |
| FLOSS.exe | 37 | Easy to run standalone version with no dependencies needed. It will additionally try to decode strings and find stack strings. |
BinText is shown here and finds strings twice for some reason.
PE Studio showing some hints about the context of a string.
Hybrid-Analysis showing a lot more strings than the static tools.
In closing, all the tools found the strings ‘hello’ and ‘sleep’ which look like they could be commands. There is also a call to CreateProcessA and an IP address which could be a C&C server. If your looking for a good command line tool my favorite was strings.py by Didier Stevens and Floss.exe by Fireeye, for a GUI tool I liked PEStudio.
References
- Link to strings.py by Didier Stevens
- Link to Strings2.exe by Geoff McDonald
- Link to BinText by McAfee, I think
- Link to strings.exe by Sysinternals
- Link to PEStudio by Winitor
- Link to Hybrid-Analysis
- Link to FLOSS by Fireeye
Follow me at @c00011011